Yi IoT Home Camera Riddled with Code-Execution Vulnerabilities
€ 20.00 · 5 (414) · En stock
Por un escritor de hombre misterioso

Five of them allow remote compromise of the IoT gadgets, so attackers can intercept video feeds and more.

RCE in IoT Devices” Identifying and Exploiting Vulnerabilities, by Land2Cyber
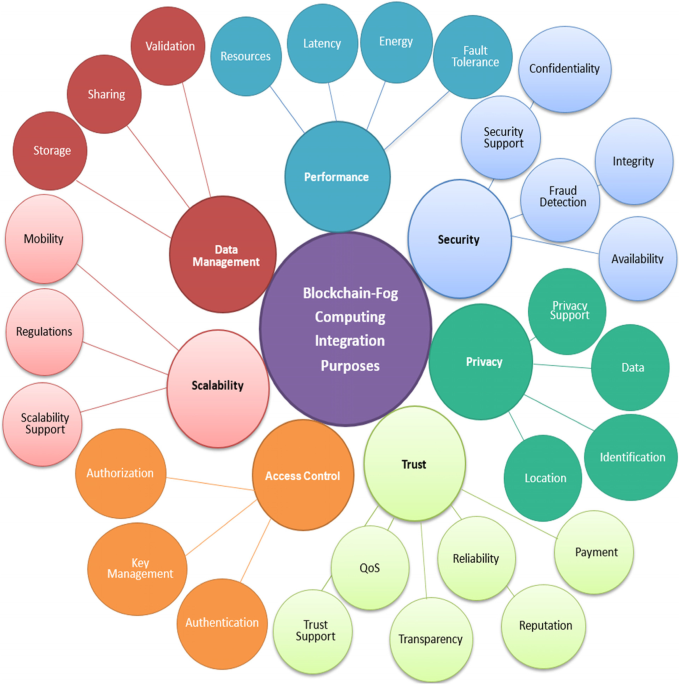
A systematic review of the purposes of Blockchain and fog computing integration: classification and open issues, Journal of Cloud Computing

5G Security System Design for All Ages
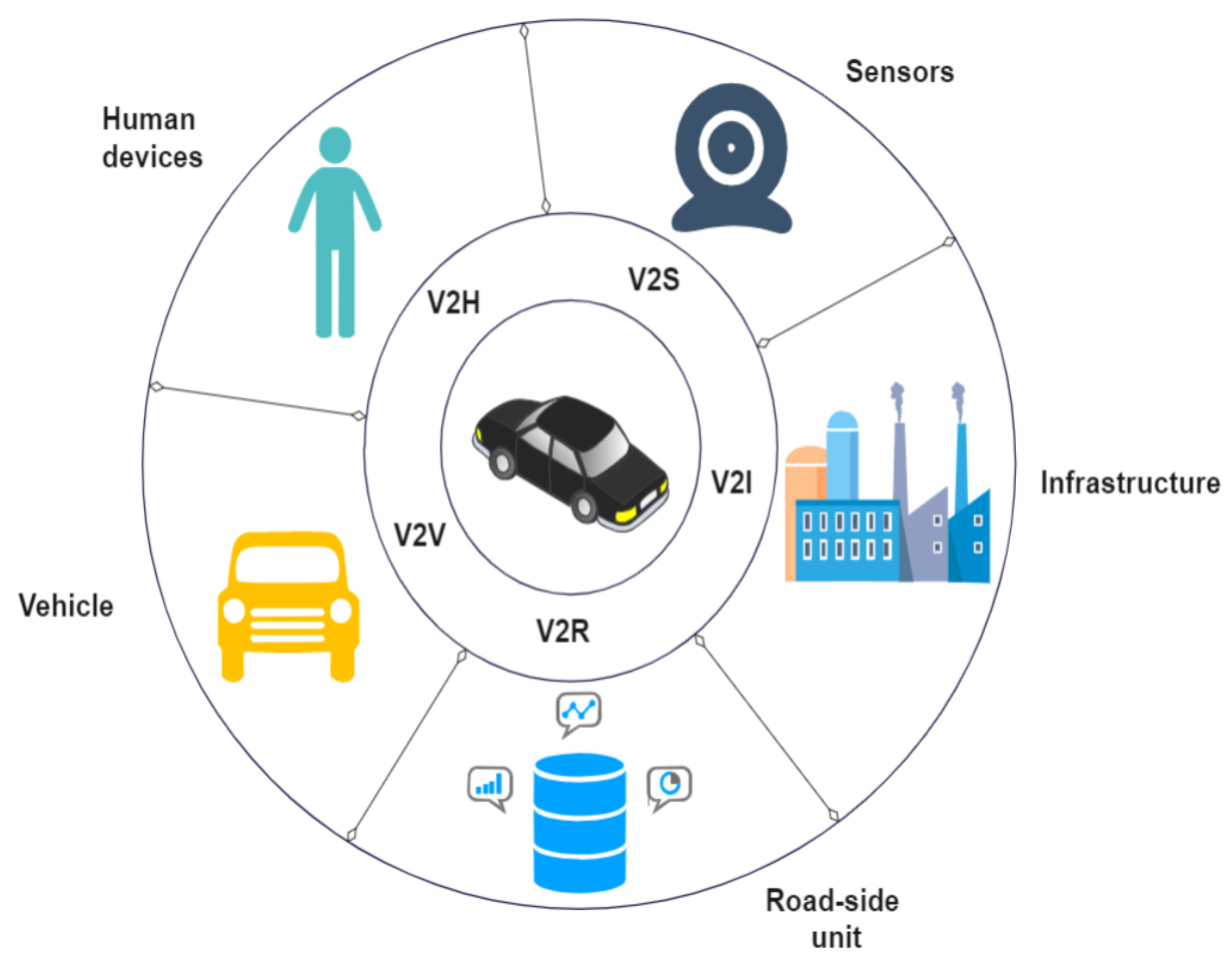
Sensors, Free Full-Text
.png)
Cyber Hygiene: Ransomware is Causing Critical Care Disruption in Hospitals - Securin
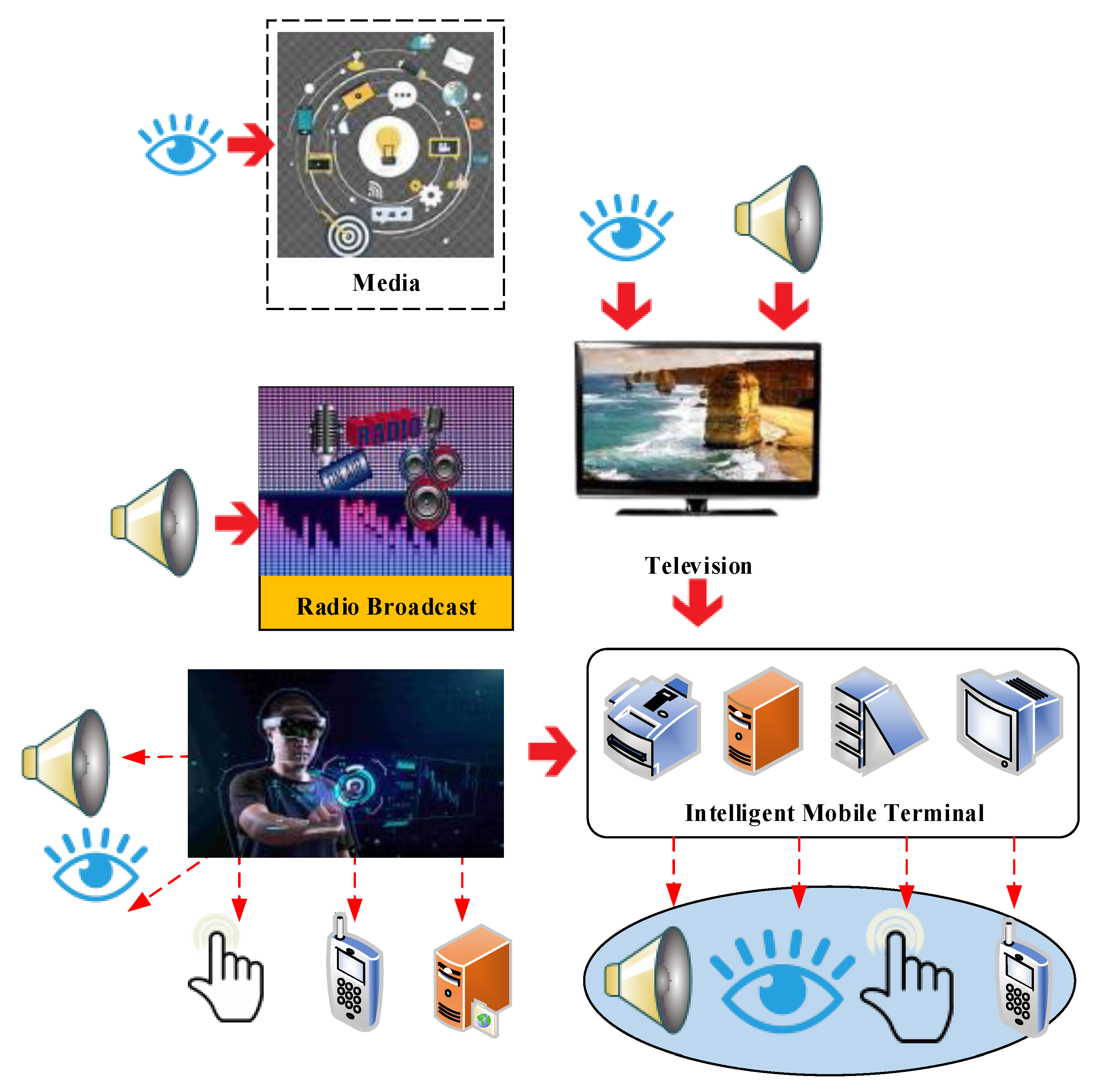
Applied Sciences, Free Full-Text

Fog computing for next-generation Internet of Things: Fundamental, state-of-the-art and research challenges - ScienceDirect

Simple Remote Code Execution Vulnerability Examples for Beginners, by Ozgur Alp
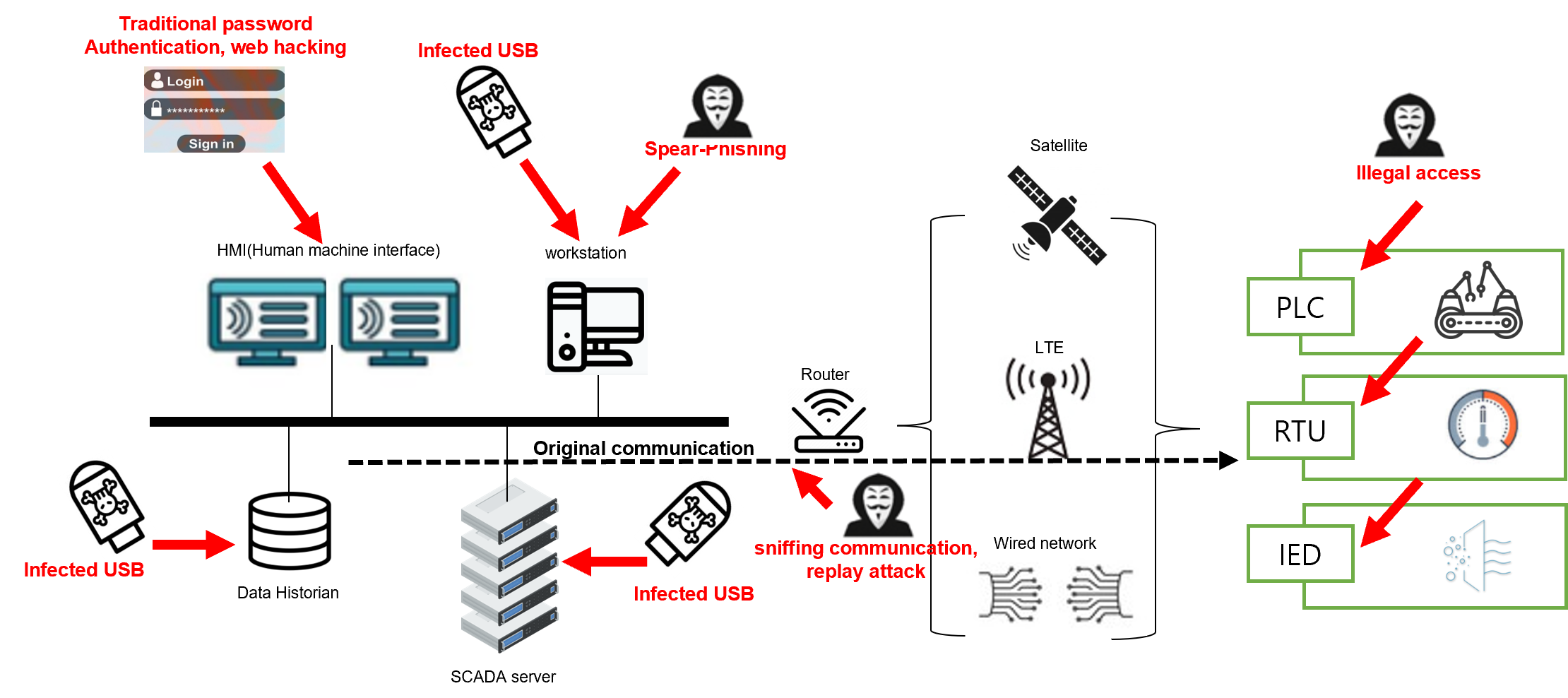
Part 1) Key security vulnerabilities in IoT environment and how to effectively counteract them

Popular IoT Cameras Need Patching to Fend Off Catastrophic Attacks

Using Images to Detect, Plan, Analyze, and Coordinate a Smart Contract in Construction, Journal of Management in Engineering

YI Outdoor Security Camera Privacy Report

A Megatrend Challenging Analytical Chemistry: Biosensor and Chemosensor Concepts Ready for the Internet of Things